
Office of Compliance Programs
Protecting PHI for Clinical Staff and Students
Revised: July 10, 2018
Introduction
HIPAA requires that LSUHSC-NO "have in place appropriate administrative, technical, and physical safeguards to protect the privacy of protected health information." {45 CFR 164.530(c)(1)}
The HIPAA Privacy Rule
A covered entity (e.g. LSUHSC-NO and its faculty, staff and students) may not use or disclose protected health information (PHI) about a patient without that patient's written authorization unless the use or disclosure falls under one of the exceptions.
What is PHI?
PHI consists of two parts:
- Information that personally identifies the patient (e.g. name, SSN, MRN, DOB, Date of Service, genetic information, etc.)
- Any information, including genetic information, whether oral or recorded in any form or medium, that:
- Is created or received by a health care provider, health plan, public health authority, employer, life insurer, school or university, or health care clearinghouse; and
- Relates to the past, present, or future physical or mental health or condition of an individual; the provision of health care to an individual; or the past, present, or future payment for the provision of health care to an individual.
What Form Does PHI Take?
PHI can be in any format, including but not limited to:
- Verbal (e.g. conversations, recordings, etc.)
- Written (e.g. computer printouts, handwritten or typed notes, filled out forms, photographs, etc.)
- Electronic (e.g. EHRs, spreadsheets, databases, digital images, online forms, etc.)
Where Can PHI Be Found?
Depending on the format, PHI can be found in:
- Electronic Health Records
- File cabinets
- Desks (e.g. papers, desktop computers, etc.)
- Hallways, waiting rooms, elevators (e.g. conversations with others or on the phone, notes dictated for transcription, etc,)
- Spreadsheets, Word documents, PDFs, databases, etc.
- Pockets (e.g. Notebooks, smart-phones, flash drives)
- Mobile devices (e.g. laptops, tablets, USB portable hard drives, etc.)
- Network file servers
- Printers, copiers, fax machines
Protecting PHI
We have an obligation to protect the privacy of LSUHSC-NO patients. Simple acts can have serious consequences. What are some of the ways to help insure PHI is protected?
Do you REALLY need to use PHI?
While using and disclosing PHI is essential for treating patients, there are many tasks that can be accomplished without using PHI. For example, the statement, "Mr. Carbuncle is ready to have his boils lanced," contains PHI. However, the statement "Mr. Carbuncle is ready for you in Room 3," does not.
Many times the use and disclosure of PHI can be reduced by simply choosing to use and disclose health information OR use and disclose identifiers, but not both. Most hospitals have banned using texts or email to communicate PHI. When the identifiers are separated from the health information, it is no longer PHI and can be sent safely.
In the example below, a resident has sent a text to an attending physician regarding a patient's lesion. The photograph does not include the patient's face or any unique identifying marks such as scars or tattoos. The text does not include the patient's name or any other identifiers. For that reason, the text does not contain PHI and is not subject to HIPAA.
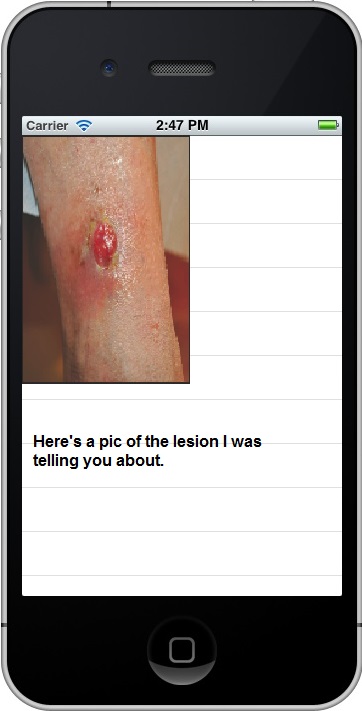
The resident then calls and discusses the case with the attending physican. He can clarify any identifiers during the call.
Scenario 1
Dr. Capaldi, a second year resident, is working the evening shift at Our Lady of Perpetual Sorrows Hospital. He is concerned about some lab values on a recently admitted patient. He phones the attending on call, Dr. Hartnell, to discuss his concerns but the list of lab values is too long to relate over the phone. Dr. Hartnell instructs Dr. Capaldi to text him the lab values. Our Lady of Perpetual Sorrows has a strict ban on texting PHI so Dr. Capaldi takes a photograph of the lab values and carefully crops out all the patient identifying information (name, MRN, etc.). He then texts the picture to Dr. Hartnell. Afterwards, Dr. Capaldi deletes the photograph from his phone. Has Dr.Capaldi violated the hospital's ban on texting PHI?
Hover your mouse over or tap your finger on the box below to see the right answer. (Tap on any picture to make the answer disappear.)
Redaction
Another method of separating identifiers and health information is redaction. Redaction is the process of obscuring or removing information from a document or record. It is a difficult and painstaking process to do correctly on existing documents and records.
- ALL instances of the information (e.g. name) and indirect references (e.g. mother’s name) to the information must be identified and redacted.
- The redaction method must render the redacted information unrecoverable.
In many cases, redaction is needed to prevent sensitive information from being breached.
- Records request (from someone other than the patient)
- Legal discovery
- Research
- Publication
- Article
- Web page
Physical Redaction
Physical redaction is applied to paper records and analog recordings. Methods include:
- Excising (cutting) the printed or recorded information with a knife or scissors.
- Erasing magnetically information from recordings.
- Obscuring information with a special redaction marker.
When excising, be sure to collect all the cuttings and ensure they are destroyed by shredding or incinerating. When blacking out sections of paper documents ensure that information has been completely obscured.
- Use a marker especially designed for redaction.
- Shine bright light on and through the paper to ensure that the underlying information cannot be viewed.
- It may be necessary to blacken both sides of the paper or photocopy the blackened page and substitute the photocopy to ensure the underlying information cannot be viewed.
Digital redaction
Digital redaction is extremely difficult to perform correctly. Most computer programs are designed to preserve information, not destroy it. The majority of computer programs used for editing text do not have a redaction function.
This requires the individual performing the digital redaction to have an in-depth knowledge of information is stored in a computer. Adobe Acrobat (not Acrobat Reader) version 9 and later has an effective redaction function. It is a two step process:
- First, mark all the information in the document to be redacted.
- Tell the program to redact the information. The program will warn you that the selected information is about to be destroyed and will become unrecoverable. You will need to confirm that is what you want before the information is actually redacted.
Digital Redaction Methods That DON’T WORK
- Highlight Function
- Using the highlight function and selecting the color black produces a document that has the same appearance as a redacted document, however,
- The information underneath the “highlight” has not been destroyed.
- To view the redacted information, simply select the whole document and highlight it in yellow.
- Track Changes- Some people choose to simply delete information from their documents and save the altered version. This is effective unless the “Track Changes” function is turned ON. When Track Changes is active. The deleted information is preserved and can be viewed, even though it is redlined.
- Password protecting a document – Most methods for password protecting a document are extremely weak and easily cracked. There are many free utilities available for this purpose.
- A search for “free Adobe password remover” produces over a million results.
- A search for “free Microsoft Office password cracker” produces over eight (8) million results.
How to Check Digital Redaction
- Search the document for the redacted information. If the search function can find it, it has not been redacted.
- Select all the information in the document and highlight in a pastel color like yellow or light green. Does the redacted information become readable?
- Copy the redacted information from the document and paste it as plain text into a blank Word document. Does the redacted information become readable?
- Ensure “Track Changes” is turned OFF.
REMEMBER
- In order for redaction to be effective, the redacted information must be unrecoverable.
- ALL instances of identifiers in the document must be redacted for the document. If one instance of an identifier (e.g. the patient’s name, DOB, etc.) is missed, the document is considered identified information.
- For digital documents, use the search function to identify all instances of identifiers.
- For paper documents search the document from beginning to end and then from end to beginning. Get help from co-workers and fellow students in reviewing documents for identifiers.
When You Really Need to Use PHI
What about when it's not feasible to separate identifiers from health information and you need to use and disclose PHI (which is most of the time)? It is your responsibility to take reasonable precautions to help insure that PHI remains confidential. What are some of the precautions you can take?
Verbal
- Never discuss a health information with a patient when others are present in the room unless you have cleared it with the patient first. Discussing health information with a minor child and her/his parents is an exception.
- When it is anticipated that you will be speaking with relatives without the patient present (e.g. the patient is having surgery or other procedure), discuss this with the patient beforehand and find out if the patient has any concerns about her or his health information being shared with loved ones.
- When discussing the patient's condition, whether it is a discussion with relatives or colleagues, move out of earshot of others and keep your voices low to avoid being overheard.
- Close exam room doors or pull curtains in patient rooms when patients are being examined/treated.
- On the Phone
- If at all possible, do not to use patient identifiers when discussing a case on the phone.
- Be aware of your surroundings when discussing patient information on the phone:
- Check to see if anyone is within earshot
- Use a low tone of voice
- When leaving a voice-mail message, leave the minimum information necessary. Someone other than the patient may listen to the messages.
- Do NOT leave any information about a patient’s diagnosis or treatment on a voice mail.
- A message like, “Please call Dr. Smith’s office at your earliest convenience.” is fine.
- A message like, “Please call the LSU Clinic,” is fine. (No indication of diagnosis or treatment.)
- A message like, “This is Dr. Smith calling with the results of your STD test.” is not acceptable.
- A message like “Please call the HemOnc clinic as soon as possible.” is not acceptable. (Specialty clinics reveal information about the patient’s diagnosis and treatment.)
Written
- Loose pieces of paper being transported from one place to another should be secured in an envelope or folder to prevent them from slipping out.
- Papers with PHI should not be left lying around in unsecured areas.
- Papers with PHI should not be brought outside the hospital unless they are being transported from one place of business to another in a secure manner.
- Always dispose of paper PHI in the shred bin.
- If you use a shredder in your office, it must be cross cut shredder that produces confetti, not long strips.
- Don't bring paper with PHI home.
- If you have documents with PHI in your work area, make sure that they are placed face down or otherwise concealed when not in use.
- Make sure that any room that has medical records in it is always attended by an employee. If there is not an employee with the records, store the medical records in a locked room or cabinet.
- If medical records are transported from one location to another, ensure that they are secured, cannot be dropped during the transport, and are not left unattended in hallways, patient waiting areas, parking garage of the hospital etc.
- Be aware that written PHI can show up in places other than paper. For example, a view box with an x-ray can also show PHI since the patient's name is usually noted on the x-ray.
- Be cautious of printed patient information, billing sheets, lab reports, notebooks with handwritten notes, report sheets for notes about patients, etc. These are items that are often left unattended in areas that are accessible by patients. They are also items that are often accidentally dropped and found by others.
- Faxes
- Verify that you have the correct information before you send it.
- Verify that the fax number you are using is current and correct.
- Always use a fax cover sheet.
- If it is a frequently used number, consider pre-programmed numbers (once they are verified).
- Call to make sure the intended recipient received the fax.
- Only send the required information.
- Make sure to update pre-programmed numbers on a regular basis.
- Mailings
- Only send the minimum information necessary.
- Verify that the right information is being sent to the right person.
- Information Handed Directly to the Patients
- Verify that you have the correct information going to the correct recipient.
- Use two identifiers to ensure you have the right patient.
- Thumb through the papers being sent to make sure one patient's information is not "stuck" to another
- PHI may be found on items such as arm bands, prescription bottles, and IV bags. Make sure that none of these are discarded in the regular trash. IV bags should have pull away labels that once torn from the bag can be disposed of in the shred bin.
- Paper PHI should be disposed of in shred bins. A few points about shred bins:
- Make sure that any shred bin that you use is locked.
- Keys should not be left in the shred bin.
- If the shred bin is so full that you can pull papers out of it, immediately notify the department that is responsible for emptying the shred bin.
- For those emptying the shred bin, make sure that any bags of paper are in a secure, locked location while awaiting pick up from the shredding company.
- When working with disposal companies, verify the identity of the disposal company employee before turning over any PHI.
- REMEMBER: The paper in the shred bin has patient PHI, and is just as important to secure as a patient's medical record.
Electronic
- Do not write your password down and place it around the computer for others to use or discover.
- Do not share your password with others.
- Do not download patient information onto jump drives or personal mobile devices that are not encrypted.
- Do not download patient information into folders that are not secured by LSU HCSD/HSC-NO Information Technology staff.
- If you have a laptop, do not store patient information on it unless it has been encrypted.
- Do not store PHI on personal laptops without expressed knowledge and permission of the healthcare institution.
- If possible, face your computer monitor away from public viewing, or use a privacy screen over the monitor.
- Do not leave screens open that contain patient information if you are not actively working on the computer.
- Ideally, PHI should remain on LSUHSC servers and accessed through Citrix or the VPN (remote.lsuhsc.edu).
- All electronic devices should be secured at all times. Lost or stolen electronic devices account for the majority of reported HIPAA breaches in the United States.
- The best defense is to not store PHI on such devices unless the device(s) is encrypted.
- If you carry a mobile device that has access to patient PHI, it should be password protected and encrypted.
- Emails
- Verify the individuals listed in the To:, CC:, and BCC: fields are the ones who are authorized to receive the information.
- Thoroughly inspect any and all attachments to ensure the information is appropriate for the intended recipients
- Check with the IT department or your computer supporter before disposing of computers and portable storage devices such as thumb drives.
- Verify that processes are in place to ensure PHI is wiped from the hard drive memory of copy machines and biomedical equipment (the vendor may be contracted to do this for you).
- If a large amount of patient information needs to be shared, you can use secure computer folders or links. Contact your IT department for more information on this option.
- To share large files securely with outside entities, use LSU Health FileS (File-Sharing Solution).
- If you do use folders in Public Folders, or on certain drives on your local workstation, remember that identifiable patient information should not be stored there unless the folder has sufficient security to limit access to only those who need it.
Other Concerns
Pictures of Patients
- Check the policy at the institution where you are working regarding photographing patients to fully understand what is or is not acceptable.
- In many cases, the patient must provide written consent before a picture may be taken.
Strangers
- Hospitals and health care facilities are bustling places, with people moving quickly about everywhere.
- In such an environment, it would be easy for someone to go unnoticed while attempting to steal PHI.
- Should anyone come to you, with whom you are not familiar, asking for access to PHI, or to restricted areas within the hospital or health care facility where you work, it is important to verify their identity.
- If you have not been notified by your supervisor that there is someone who will need access to an area or information, verify with your supervisor, Security, Hospital Administrator or the Compliance department at the hospital or health care facility where you are working before granting them access. This is true, even if the person appears to have proper identification.
- If you have not been notified by your supervisor that there is someone who will need access to an area or information, verify with your supervisor, Security, or the Compliance department at LSUHSC-NO before granting them access. This is true, even if the person appears to have proper identification or the proper authority.
Accessing Records
Each of us only has authorization to access PHI based on a need to know basis for the purpose of fulfilling our job responsibilities. Unfortunately, some take advantage of various sources of PHI to satisfy curiosity or other motives instead.
LSUHSC-NO faculty, staff and students may find themselves working and/or training in facilities that use electronic health record systems that are shared by multiple, independent health care providers. An example of such a system is the PELICAN electronic health record. In such cases, an individual must be granted permission to access the electronic record in writing by the facility that owns the record, in addition to having a job related need to view the information before accessing the electronic record.
No matter why an employee or physician accesses PHI, if there is not a job specific reason to do so, the access is prohibited by LSU policy, and the HIPAA regulations! This includes access to family members’ information, including spouses, parents, adult children, siblings, significant others, coworkers, etc.
Any such unauthorized access would be a direct violation of HIPAA regulations, and expose the person who violated them not only to disciplinary action, but also to possible legal action.
If you are the caregiver of a family member or friend and need access to PHI, then a release of information form signed by the patient should be given to medical records so that you can be given information on the patient by medical records.
Possession of Records
- What identified patient information do you have in your possession?
- To whom does this information belong?
- The patient
- The hospital or other health care institution
- Do you have right to have that information in your possession?
- Are you treating the patient.
- Do you have written authorization from the patient or the hospital to possess this information.
- When should patient information in your possession be destroyed, de-identified or turned over to the health care institution?
- When the treatment relationship ends.
- Change in rotation
- Change in employment
- In certain instances, at the end of the research study, if these are research records. (see CM-53 Section S)
Social Media
LSUHSC-NO recognizes that social networking websites and applications (i.e. Facebook, Twitter, and YouTube, etc.) are an important and timely means of communication. However, LSUHSC-NO faculty, staff, residents, and students who use these websites and applications, must be aware that the protections of patient information required by HIPAA apply to social media as well.
While it is popular to share events that happen at work or school on social media outlets in the form of posts, pictures, and/or videos, employees and students of LSUHSC-NO must be vigilant to ensure that patient information is NOT compromised in the process. Some ways to prevent PHI from being exposed on social media include:
- Ensure that all personal identifiers are removed (e.g. age, gender, race, before and after photographs and/or tattoos), and are NOT inadvertently included in any social media.
- Be familiar with the hospital's social media policy. It may have different restrictions than LSUHSC-NO's policy.
- In the absence of a policy, care must be exercised when posting information for educational purposes to ensure that any information posted combined with other readily available information (ex. address, telephone number, etc.) will NOT result in the identification of the patient.
Policies of Affiliated Hospitals
The HIPAA regulations allow hospitals to use a combination of physical, technical and administrative safeguards as necessary to protect PHI. When working in a different hospital, be mindful of the possibility that the hospital’s HIPAA policies may be different from those at LSUHSC-NO. .
For example, LSUHSC-NO allows access to its network from outside the campus because it has a technical control called a virtual private network (VPN) in place. Another hospital may choose not to incur the cost of a VPN and use an administrative control in the form of a policy that forbids accessing the hospital network from outside the campus. When working at another hospital, it is your responsibility to familiarize yourself with that hospital’s policies and ensure that they are followed.
Breaches
If you become aware of a breach of PHI or suspect a breach may have occurred, it should be reported immediately to:
- The Compliance/Privacy Officer in the Office of Compliance Programs at LSUHSC-NO, and
- The appropriate official at the institution where the breach occurred if other than LSUHSC-NO.
Compliance will conduct a risk assessment to determine if the breach must be reported to the patient and the U.S. Department of Health and Human Services.
Timely notification of any known breach is CRITICAL as we only have 60 days from the discovery of the breach to take the necessary action required by the Breach Notification Rule.
Getting Help
If you have any questions, please contact the Office of Compliance Programs by:
- Email: nocompliance@lsuhsc.edu
- Phone: (504) 568-5135
- Anonymous Hotline: (504) 568-4367
- In Person: RCB, suite 807
- Website