
Office of Compliance Programs

Information Security Training on Malware
Revised April 23, 2018
Introduction
Welcome to LSUHSC-NO’s Information Security online tutorial on Malware. All employees, students, and affiliates of the University who use the LSUHSC IT Infrastructure in the course of their work or studies are required to complete this training on an annual basis.
Purpose
The primary goal of this tutorial is to help raise your awareness on how to recognize malicious software and take proper action to prevent its disruptive effects. LSUHSC cannot protect the integrity, availability, and confidentiality of its information without the informed participation and support of everyone! You are the last line of defense in identifying and eliminating malicious software. Training is the key to that defense so it is important that you stay up-to-date with your compliance training.
What is Malware?
Malware (short for “MAL"icious soft"WARE") is any software
designed to
infiltrate a computer system and perform actions without the user's
informed consent. It can enter your computer or digital device as the
result of
clicking on website links,
pop-up ads, toolbars, games, emails, or any other normal computer
activity.
How Does Malware Infect a Computer or Digital Device?
- Email Attachments
- Infected Web Pages
- Infected Digital Media (USB drives, memory cards, DVDs, CDs, etc.)
- Malware disguised as utilities or games (Trojans)
- Messages and pop-ups that trick you into downloading malware (scareware)
- Text messages
What Can a Hacker Do If Your Computer Becomes Infected with Malware?
- Spy on your computer activities
- Steal your passwords by logging your keystrokes
- Steal your identity
- Read your email
- Cause irreversible destruction to your current applications, files and data
- Infect others by attaching itself to your outgoing correspondence and files
Motivation for Malware
- Pranks
- Spamming (unsolicited junk email)
- Stealing data
- Fraud (bank, credit card, etc.)
- Vandalism
- Extortion

KNOW YOUR ENEMY!
Malware authors use several common tricks to install malicious software on your computer or digital device. Understanding the most common ways they do can help you stay protected. Examples of Malware include:
- Viruses
- Worms
- Spyware
- Keystroke loggers
- Rootkits
- Trojans
- Hybrid Malware
- Scareware
Viruses & Worms
Viruses are programs that copy themselves to a PC or laptop and install themselves without the user’s knowledge or consent. They can be transmitted as attachments to an e-mail or in a downloaded file, by clicking on a link to an infected website or be present on digital media such as:
- External hard drive
- USB or 'thumb' drive
- Flash memory cards such as:
- Secure Digital Card (SD, SDHD, SDxD, miniSD, microSD)
- Memory Stick (Duo, PRO-Duo, PRO-HG Duo, Micro M2)
- xD Picture Card
- PC Card (PCMCIA)
- CompactFlash
- Smart Cards
- MultiMedia Card (MMC, MMCmicro)
- Optical media (CD, DVD, Blu-Ray)
A worm is a virus that replicates itself by resending itself as an e-mail attachment or as part of a network message. They usually take advantage of security holes in the operating system or software package.
Virus Infects UPS Stores
In August 2014, United Parcel Service announced that customers of UPS Stores in 24 states may have had their credit card information exposed by a computer virus. An investigation revealed that information on approximately 100,000 transactions had been compromised.
Spyware

Spyware is the class of programs that:
- Monitor your computer usage habits and report them back to a company that stores this information in a database for marketing purposes.
- Are installed with little or no notification during the installation of another program or while browsing the Internet.
- Open advertising windows when browsing the Internet.


Keystroke Loggers
There are two types:
- Hardware Keystroke Loggers- hardware devices installed between your keyboard and computer.
- Software Keystroke Loggers- software programs that log every keystroke typed and transmit them back to their home base.
Keystroke Logger Leads to Health Data Breach at Kentucky Hospital
On September 16, 2015, Muhlenberg Community Hospital was notified by the FBI of a keylogger cyberattack which lead to a health data breach. An investigation revealed that a software keylogger had been installed on several hospital computers and may have been on the computers as early as January 2012.
Data compromised included patient:
- Names
- Addresses
- Telephone number
- Dates of birth
- Social Security numbers
- Driver’s license/state identification numbers
- Health plan information
- Financial account numbers
- Credit card information
- Employment information
Compromised employee and contractor information included:
- Credentialing information
- Drug Enforcement Administration numbers
- National Provider Identifiers
- State license numbers
- User names
- Passwords

Rootkits
A Rootkit is software that enables continued privileged access to a computer while actively hiding its presence from the user by subverting normal operating system processes. They are made up of one or more programs designed to perform any of the following functions:
- Obtain administrator privileges on the system.
- Create a “backdoor” to allow the cybercriminal easy administrative access to a computer or network whenever he desires.
- Delete any log entries or other records that may reveal the existence of the rootkit to the legitimate owner of the system.
- Collect and report User IDs and Passwords to would be hackers.
Rootkits are used by cybercriminals to:
- Launch attacks on websites or networks.
- Send spam emails.
- Distribute copyrighted materials such as music, videos, or commercial software.
- Steal passwords to other online accounts.
- Harvest user habits.
- Execute financial transactions.
Chinese Cybercriminals Breached Google Play To Infect Android Devices
In August 2015, a group of Chinese hackers uploaded a Brain Test app to the Google Play store. The app installed a rootkit which allowed the app to reinstall itself after the user deleted the app. The rootkit included a backdoor to allow its creators to install further malware. Somewhere between 200,000 and 1 million devices were believed to be infected. The rootkit can only be removed by re-flashing (i.e. performing a factory reset) the device.

Trojans
Like their ancient Greek namesake, Trojans are programs that appear to be one type of program (e.g. a screensaver) but are hiding additional functions of which the legitimate user is completely unaware. These functions can include:
- Giving administrator access to the cybercriminal author of the Trojan.
- Reporting everything viewed on your screen or typed on your keyboard (e.g. passwords) to another computer on the Internet.
- Running additional programs on your computer.
40 Million Credit Card Accounts Exposed in Attack on CardSystems Solutions
In June 2005, hackers compromised CardSystems Solutions database using an SQL Trojan attack. This attack inserted code into the database every few days through a browser page, placing data in a zip file and sending out via the Internet’s File Transfer Protocol. Hackers gained access to names, accounts numbers, and verification codes of 40 million credit card users.
Hybrid Malware
The differences among types of malware are becoming less important because most hackers don't restrict their code to just one type of malware. Most attacks use features of viruses, worms, Trojans, spyware, phishing, and bots. For example, the replicating features of a virus can be combined with remote control features of a Trojan and the administrative functions of a rootkit to create a program that spreads like a virus, then “phones home” for instructions, then causes the victims computer to carry out those instructions.
Ransomware
A recent development in hybrid malware is Ransomware. The goal of ransomware is not to steal your data but hold it hostage. The hacker uses one of the previously discussed methods to install an encryption program on your PC. Once all the files are encrypted, the encryption keys are transmitted to the hacker and a message similar to the following is displayed:
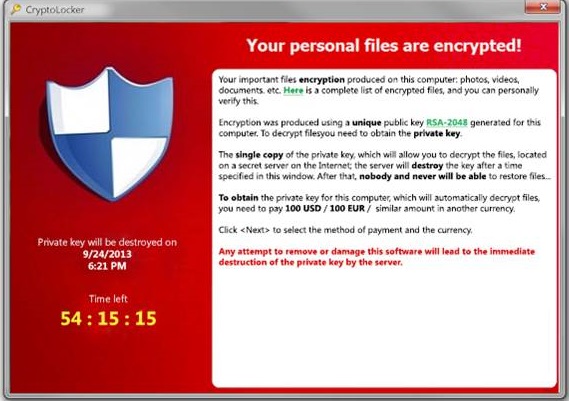
(Click or Tap on image for expanded view)
Ransomware Facts
- The encryption method utilizes very sophisticated algorithms that are extremely difficult to crack.
- While older versions of ransomware had vulnerabilities that could be used to crack the encryption, hackers have corrected these flaws in the latest versions.
- Any shared drive that is mapped to the computer as a letter (e.g. “T:\ drive”) will be encrypted.
- Payment will usually be demanded in Bitcoin.
- Hackers are generally prompt in providing the decryption keys once payment is made.
- Payment encourages further attacks.
Signs of a Ransomware Attack
- Extensions of filenames are changed (e.g. "file.xls" is changed to "file.mp3").
- Your computer becomes sluggish and the hard drive activity light stays on.
- A message pops up on your screen (like the one above) demanding payment.
What To Do if Infected with Ransomware
- Isolate the infected computer immediately. Infected systems should be disconnected from the network as soon as possible to prevent the ransomware from attacking network or shared drives.
- Contact the Helpdesk, (504) 568-HELP immedialtely.
Hospital Pays $17,000 for Ransomware Encryption Key
On February 5, 2016, employees of Hollywood Presbyterian Medical Center in Los Angeles reported being unable to get onto the hospital's network. The malware blocked access to certain systems, including the hospital’s electronic medical record, as well as electronic communications. The hospital staff had to revert to paper for all operations/communications. After trying for ten days to defeat the encryption, hospital executives agreed to pay the ransom of 40 bitcoin (approx. $17,000).
Zero Day Malware
Zero Day malware refers to brand new or previously unknown malware. Because zero day malware is new, anti-virus and spyware scanner programs that depend solely on signature recognition cannot provide any protection. In recent years, foreign governments and organized crime have joined the ranks of malware programmers in searching for new vulnerabilities in software. This has tremendously increased the resources available for researching and developing new types of malware. As a result, the occurrences of new malware are increasing at an alarming rate. The STUXNET virus that infected computers used in Iranian nuclear plants contained exploits from four previously unknown vulnerabilities in Microsoft’s Windows Operating System.
Suspicious Email
Suspicious email includes:
- Any email you receive with an attachment.
- Any email you receive from someone you don’t recognize.
Steps to combat malware from infecting your computer by email include:
- Removing Administrator Privileges from the login ID you use on a daily basis. This will prevent any software from being installed without your explicit permission.
- Note: Use a separate login ID for tasks that require administrator privileges.
- Disabling auto-preview and the preview panel in your email client.
- Setting your email client to read all mail in plain text.
- Saving all attachments to your computer and scanning them with your anti-virus product before opening them.
- Note: The website VirusTotal.com allows the user to submit a saved file for examination by multiple anti-malware programs.
Frequently, emails will try to trick the recipient into installing malware by:
- Posing as a law enforcement or other government agency.
- Including official-looking insignia.
- Informing the recipient of some event (e.g. “You have been sued.”) and direct the recipient to open an attachment or click on a link for more information.
The malware will take the form of either:
- An attachment that, when selected, will install the malware on the victim’s computer.
- A link that, when selected, will direct the browser to an infected website which will install the malware.
- Note: The website VirusTotal.com allows the user to submit a website address (URL) for examination by multiple anti-malware programs.
A hacker will often send a suspicious email will via a third-party file sharing service. This makes it more difficult to trace the email back to the hacker.
If You Suspect an Email is Suspicious, You Should:
- NOT use any links or open any attachments.
- NOT take any action directed in the email.
- Check its legitimacy -by a method you know to to be legitimate - or contact the sender separately by a method you know.
- If you are unable to verify the legitimacy of an email, send the email as "an attachment" to spam@lsuhsc.edu, and delete it from your Inbox.
Scenario

You see the following email arrive in your inbox:
- Pond, Amelia
- Amelia Pond shared a document with you "Outstanding Invoice"!!!
- *EXTERNAL EMAIL; EVALUATE* Please find attached and get back to me as soon as possible.
You know that Dr. Pond is the head of a sister agency with which LSUHSC-NO conducts business. You open the email and find the following:
- From: Amelia Pond [mailto:apond@sisteragency.la.gov]
- Sent: Friday, March 16, 2018 9:54 AM
- To: Amelia Pond [apond@sisteragency.la.gov]
- Subject: Amelia Pond shared a document with you"Outstanding invoice"!!!
- *EXTERNAL EMAIL: EVALUATE*
- Please find attached and get back to me as soon as possible.
- Regards,
- Amelia
You know of Dr. Pond but your office does not have any dealings with her. Her agency is not a part of LSUHSC so the "*External Email; Evaluate*" message is expected. A PDF file is attached. Should you open it?.
With money being so tight, we need to pay them promptly.
There's something that doesn't feel right.
Hover your mouse over or tap your finger on the box below to see the right answer. (Tap on any picture to make the answer disappear.)
There are several things about this email that raise suspicions:
- First and foremost, if your department doesn't have dealings with Dr. Pond or her agency, why is she sending you the email?
- Your email address doesn't appear in the "To:" line yet you received the email.
- Dr. Pond's email address is the only email address in the "To:" line. This is often done because the sender wishes to keep the list of recipients hidden from each of the other recipients. This indicates you were not the only person to whom this email was sent.
- The subject line is: "Amelia Pond shared a document with you"Outstanding invoice"!!!" "[Name shared a document" is a phrase that many third party file sharing services insert in the subject line of the emails they send, indicating that Dr. Pond's email address may have been forged.
The appropriate course of action is to contact Dr. Pond by some method other than email (e.g. by phone) to confirm that the email was actually sent by her. If it was not, send the email as "an attachment " to spam@lsuhsc.edu, and delete it from your Inbox.
Infected Websites
Malware can also infect websites. Any unprotected computer that browses an infected website will become infected. Even well-known and respected websites such as the NewYorkTimes.com and bbc.com have been infected.
Scareware
One of the signs of an infected website is a scareware message that pops up in the middle of your browsing. Scareware is a message designed to scare you into installing malware on your system. The following is an actual scareware message that is designed to look like a message from the Windows Security Center.
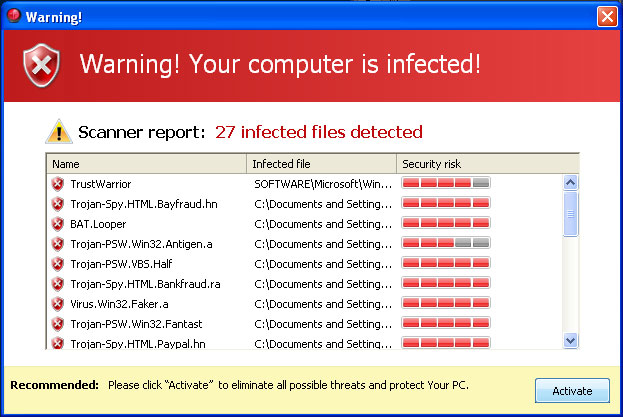
(Click or Tap on image for expanded view)
The following Scareware message appears when surfing an infected website. It appears to be a warning from your anti-virus program. The message is a fake. The number of infections "found" is set to a large number deliberately to shock and scare the user. However, clicking on ANY of the buttons (including the “OK” in the lower right corner) will cause malware to be installed on your device. The best course of action is to power off your device. If you device is a Windows computer, power off without selecting the "Shut Down" menu option.
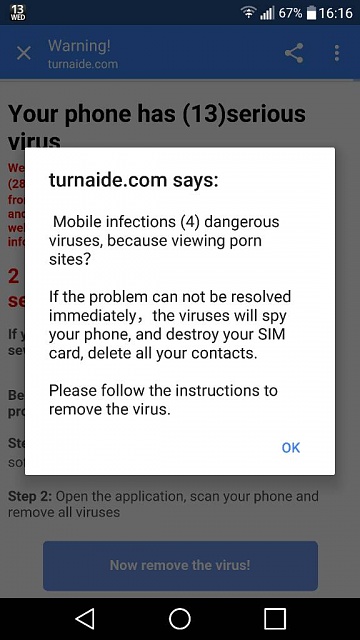
(Click or Tap on image for expanded view)
How Can YOU Tell if a System Message is Scareware?
Ask yourself the following questions:
- Are there grammatical errors in the message?
- Does the message refer to some catastrophic event? (e.g “Your registry is damaged!” or “Your computer is infected”)
- Does it instruct you to go to an unfamiliar website? (e.g NOT microsoft.com or lsuhsc.edu)
- Does it ask you for payment? (e.g. credit card, PayPal, etc.)
- Does it instruct you to download and install a program?
- Does the anti-virus warning match the name of your anti-virus software?
If any of the above are TRUE, then it may be Scareware. Call the Help Desk or your computer supporter to make sure.
Make sure your browser is set to always start from a home page selected by you and does not restore previously visited websites.
Warning Signs YOUR Computer Might Be Infected
- Your browser homepage changed unexpectedly.
- Persistent and unexpected pop-up windows when your browser is open.
- Alerts from your anti-virus program that there is malware on your computer.
- Odd behavior such as your computer suddenly becoming very slow and unresponsive with no obvious explanation.
- Windows opening by themselves.
- Unexpected new icons appear on your desktop.
- Unusual toolbars added to your web browser.
- Applications start failing to launch properly.
- Your email account sends out messages to your contact list that you did not send.
Contact your computer supporter or the Help Desk if you suspect your computer has malware installed.
How To Protect Yourself from Malware
Follow these steps to reduce the risk of your devices being infected with malware:
- Ensure up-to-date anti-virus software is installed on you computer (LSUHSC provides anti-virus software with updates to all university owned computers).
- Ensure up-to-date anti-spyware scanner software is installed on your computer (all LSUHSC owned computers have antispyware software installed which is updated regularly).
- Ensure operating system and software patches are up-to-date on your computer (LSUHSC automatically updates all operating system patches on university owned computers).
- NEVER open email attachments unless you can verify the sender and you trust them.
- NEVER click on the links in spam email.
- Scan ALL downloaded files with your anti-virus program regardless of the source and file type.
- Send suspicious emails "as attachments" to spam@lsuhsc.edu, and delete them from your Inbox.
- Ensure applications such as Adobe Reader or Flash are up-to-date with all patches.
- Ensure that your LSUHSC User ID is NOT a local administrator on your PC or laptop (contact your computer supporter for more information).
- Don't give sensitive, personal, financial, log-in, business, system or network information to anyone you don't know or who doesn't have a legitimate need for it.
- Always check your computer for anything unfamiliar that may be plugged in.
- Use caution with your Internet surfing habits. Avoid questionable websites. Some sites may automatically download malicious software on to your computer.
- Think before you click! Never click on pop-up alerts. Don't even click on the red "X" to delete the pop-up alert as this may result in the installation of malware.
- Turn on Internet Explorer’s SmartScreen filter. (This is the default on LSUHSC owned computers.)
- Bookmark (or add to your favorites list) trusted websites and access these websites via these lists or bookmarks.
- Be sure to back up your work.
- Read each panel of any software installation process carefully to ensure that it is not installing any software other than what your requested.
- Stay watchful and speak up if you notice strange happenings on your computer.
- Make sure that any computer you use to access LSUHSC’s network remotely (from home or while on vacation, or at a conference) has incorporated all of the precautions listed above.
As a Recap
- A great deal of malware can be avoided through simple awareness practices.
- Make sure your computer is protected with up-to-date anti-virus and anti-spyware software.
- Make sure your computer, devices, and applications are current and up-to-date.
- Beware of web pages that ask or attempt to install software. Unless you are very certain of the website and the software being offered, do NOT install it.
- Never respond to suspicious email or click on any included links.
- Practice safe Internet browsing.
- Send suspicious emails "as attachments" to spam@lsuhsc.edu, and delete them from your Inbox.
- The ultimate defense is a well-informed user (like YOU) who can recognize malware and take the proper action.
- If you are unsure about what to do, please ask for help. Contact your computer supporter or call the Help Desk (568-HELP).