
Office of Compliance Programs
Information Security Training for Appropriate Use of Cloud Computing Services
Protecting Yourself and Your University in the Digital World
Revised July 10, 2018

Introduction
Welcome to the LSUHSC’s Information Security training module on the appropriate use of Cloud Computing Services. It is intended for all employees and students who have access to LSU’s computing resources and must be renewed on an annual basis.
Cloud computing is becoming the norm for managing information. It offers increased opportunities for collaboration, access to extremely large data sets and immense computing power for simulation and problem solving. Along with these opportunities come increased risks to the security of information. If appropriate precautions aren’t taken information about your students, patients and co-workers, as well as your own personal data can be breached.
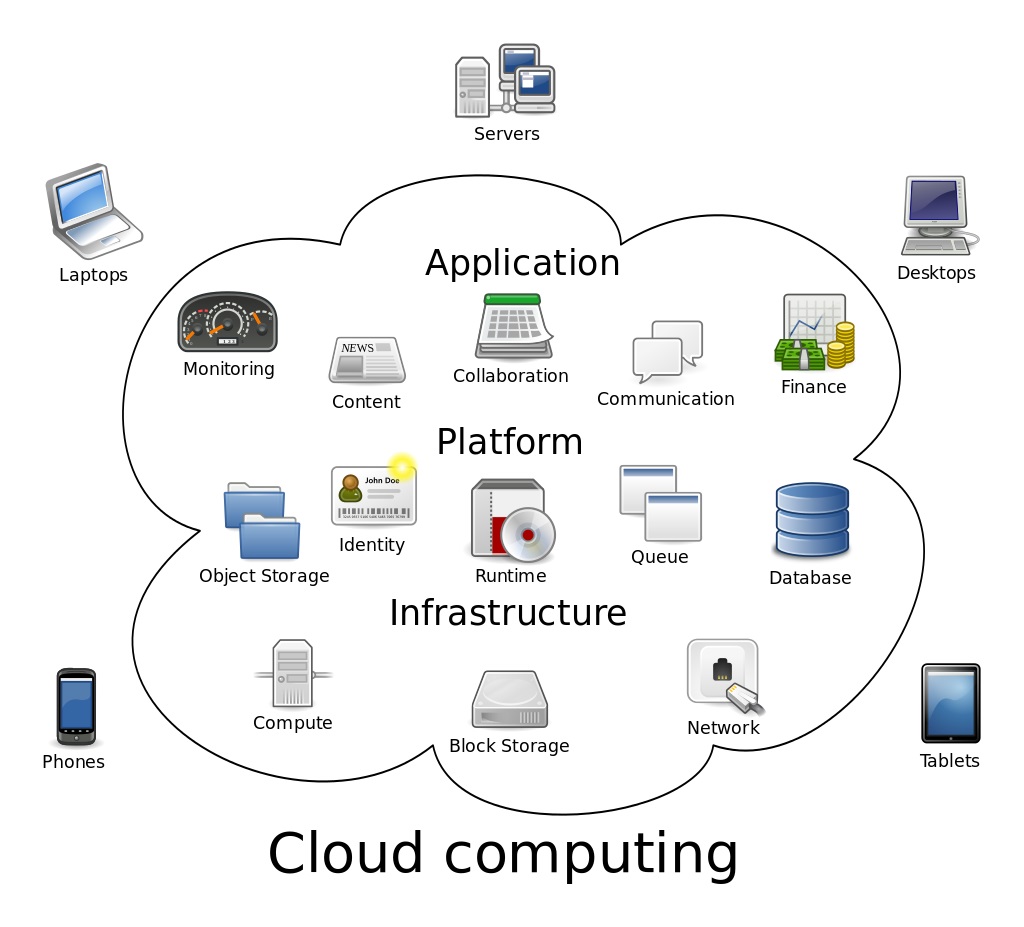
(Image credit:By Sam Johnston - Created by Sam Johnston using OmniGroup's OmniGraffle and Inkscape (includes Computer.svg by Sasa Stefanovic)This vector image was created with Inkscape., CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=6080417
(Click or tap image for expanded view)
What is Cloud Computing?
- In the simplest terms, cloud computing means storing and accessing data and programs on another computer over the Internet instead of your own computer's hard drive (aka “C” drive).
- “The Cloud” is just a metaphor for the Internet.
- Cloud computing enables companies to consume computer resources as a utility -- just like electricity -- rather than having to build and maintain computing infrastructures (servers, mainframes, backups, etc.) in-house.
- "The Cloud" is another name for "Someone Else's Computer"

What You Need to Know
- Goals for this training
- Examples of Cloud Services
- Accessing Cloud Services
- Laws Governing Use of Information at LSUHSC-NO
- Shadow Computing
- Use of Personal Accounts
- Information Classification
- Cloud Service Providers and the Law
- Cloud Services Carry Their Own Security Risks
- Requirements for Using Cloud Services for LSUHSC-NO Data
- Breaches
Goals for This Training
- Educate faculty, staff and students about cloud computing.
- Provide information on how to use cloud computing services safely and securely.
Examples of Cloud Services and How They are Accessed
- Examples of cloud storage include services such as Amazon Cloud Drive, Apple iCloud, Box, DropBox, Google Drive, and Microsoft OneDrive.
- Examples of cloud software include email (Gmail, Hotmail, etc.), office suites (GoogleDocs, Office365, etc.) and HTML editors (Aloha, Maqetta, etc.)
- Examples of cloud computing platforms include Microsoft Azure and Amazon Web Services (AWS).
Accessing Cloud Services
Cloud Services can be accessed in many different ways:
- Through the browser on your desktop, laptop, tablet or smartphone.
- Using an app.
- Automatically (without the user actively choosing to use or store information in the cloud).
Be aware of any default settings on personally owned devices that may automatically copy information to a cloud drive.
- Apple products have a default setting to backup the data on devices to the user’s iCloud account.
- The Evernote app stores information in the cloud automatically.
- Many printer apps such as Google Cloud Print and HP’s ePrint actually route the data to a server on the Internet for printing.
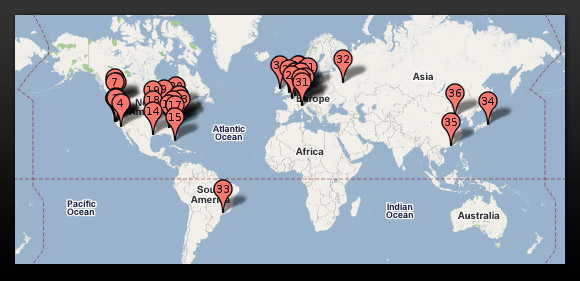
Where's My Data?
Generally speaking, if data is available on multiple devices, it means that data is stored on somewhere other than your personal device (usually on the Internet) and additional precautions must be taken if that data is to be secure.
Because digital information travels at the speed of light, the actual computer that stores information can be located thousands of miles away from the user. Many cloud service providers have facilities in different countries. It is not unusual for cloud services companies to keep multiple copies of information in different countries as part of their disaster recovery strategy.
If the information on your personal device is copied to a cloud server in another country, it is no longer subject to the protections of U.S. laws. Intellectual property, patient information, employee information and student information would lose their privacy protections.
Unless there is a contract that specifies your data will only be stored on equipment located in the United States, you have no control over where the data is located or who can access it.
Google Data Center Locations
United States
- Berkeley County, South Carolina
- Council Bluffs, Iowa
- Douglas County, Georgia
- Jackson County, Alabama
- Lenoir, North Carolina
- Mayes County, Oklahoma
- Montgomery County, Tennessee
- The Dalles, Oregon
Overseas
- Changhua County, Taiwan
- Singapore
- Dublin, Ireland
- Eemshaven, Netherlands
- Hamina, Finland
- St Ghislain, Belgium
- Quilicura, Chile
Laws Governing the Use of Information at LSUHSC-NO
Laws that govern the use and disclosure of information at LSUHSC-NO include but are not limited to:
- Public Records Law (LA R.S. 44 et seq.)
- Database Security Breach Notification Law (LA R.S. 51:3071 et seq.)
- The Common Rule (45 CFR §46)
- HIPAA (45 CFR §160 and §164)
- FERPA (39 CFR §99)
- Gramm-Leach-Bliley Act (16 CFR §314)
- Fair Labor Standards Act (29 U.S.C. 201, et seq. )
These laws have very strict requirements for:
- The length of time information must be retained.
- The protection the information must receive.
- The availability of the information.
- The methods of destruction used when the retention period has ended.

Shadow Computing
The availability of free cloud computing services makes it easy to automate many functions and make them available to multiple healthcare providers at multiple locations without having to involve the I.T. department.
- A transportation schedule to bring patients to their doctors’ appointments can be set up on Doodle.
- A list of patient admissions and discharges can be maintained on GoogleDocs.
- Shift change reports are posted to a DropBox account for the oncoming fellow.
The problem with this approach is that the cloud computing services are generally not subject to, nor compliant with, the laws and regulations that apply to information about LSUHSC patients, students, faculty and staff. LSUHSC-NO would need to execute a business associate agreement or other confidentiality agreement before these services could be used by and for LSUHSC-NO employees, patients and students.
Each of the examples described above depending upon the specific circumstances could be considered a breach requiring the patients and the Secretary of the Department of Health and Human Services be notified.
Because such services generally are not subject to and don’t comply with laws applicable to LSUHSC-NO and because such activities occur without oversight by LSUHSC-NO management, these activities are called “shadow computing”.
Using Personal Accounts
When an individual stores LSUHSC-NO related information in a personal email or online storage account, that individual becomes the custodian of that information. As custodian they become responsible for:
- Making the information available for public records requests and legal discovery requests.
- Retaining the information as required by law.
- Using proper destruction methods and procedures when the retention period has expired.
- Controlling access to the information including the access of the cloud services company (Google, Yahoo, etc.) employees.
- Maintaining backups of the information.
- Having a disaster recovery plan in place.
Keeping all your work or school related information on LSUHSC-NO network servers (e.g. "O:" drive, "T:" drive, etc.) or LSUHSC-NO contracted cloud services (e.g. One Drive for business)is the easiest way to comply with all of the above requirements.
Information Classification
To address the requirements of these laws and regulations, Permanent Memorandum 36 Louisiana State University System Information Security Plan (PM-36) provides for three classes of information:
- Protected (e.g. certain employment records, medical records, student records, etc.)
- Restricted (e.g. ongoing investigations, psychotherapy notes, disciplinary actions, etc.)
- Public (e.g. expense reports, meeting minutes, financial reports, etc.)
Courts have ruled that for purposes of e-discovery or public records requests, whether the information resides on the agency’s own devices or the personal devices of its employees. LSUHSC-NO bears the responsibility for producing the information under penalty of law. Therefore, faculty, staff and students must understand that there is no expectation of privacy regarding LSUHSC-NO related information, even if it resides on one’s personally owned device or personal email account or personal cloud account.
Cloud Service Providers and the Law
Most cloud service providers are not subject to the information privacy laws applicable to LSUHSC-NO. For that reason, patient or financial information stored on the servers of a cloud services provider without having the appropriate business associate or data confidentiality agreement in place could be considered a breach requiring the notification of the individuals whose information was exposed.
PM-36 requires that Protected and Restricted Information shall not be transmitted outside the confines of the LSUHSC network without the use of appropriate safeguards to preserve its confidentiality and integrity. Protected information shall not be shared with contractors or other business associates without an approved agreement in place governing the use, handling and disclosure of the confidential information.
The LSUHSC-NO I.T. Department maintains the necessary agreements with certain cloud providers. If you need cloud computing services, check with the LSUHSC-NO I.T. department to find out which services can be used securely for Protected and Restricted information.
Cloud Services Carry Their Own Security Risks
Cloud computing services are provided by large Internet companies such as Google, Amazon, and Apple. These companies are the favorite target of hackers.
- In August 2016, a hacker going by the pseudonym “Peace” claimed to have posted the credentials for 200 million Yahoo accounts.
- In July 2016, it was reported that 40 million iCloud accounts had been hacked and Apple devices were being held for ransom by Russian hackers.
- In January 2011, Google disclosed that hundreds of Gmail accounts had been compromised.
Mat Honan, a senior staff writer for the publication Wired.com fell victim to a multi-pronged attack by hackers against the cloud services he used. The perpetrators needed only Honan's Apple ID email address, billing address, and the last four digits of his credit card to wreak havoc on his digital life. In the space of one hour, the hackers succeeded in:
- Deleting his Google account
- Using his Twitter account to broadcast racist and homophobic messages.
- Erasing all the data from his iPhone, iPad and MacBook.
In one respect, Mr. Honan was lucky. There was enough information in his cloud services accounts for someone to steal his identity, clean out his bank account and charge up his credit cards. However, all they wanted was control of his Twitter account.
Hackers are not the only concern. If you are using a cloud computing service that is also being used by individuals targeted by law enforcement, you may lose access to your data. In 2011, the FBI seized 62 servers in a raid on the offices of a Swiss company DigitalOne in Reston, VA as part of an investigation into the LulzSec hacker group. As a result of the seizure, cloud services for 120 companies, unrelated to the hacker group, were taken offline and remained offline for several days.
In 2009, the FBI seized all the servers in Dallas data center operated by CoreIP. The raid shut down the servers of 50 businesses.
In 2012, Hurricane Sandy caused outages in several online services including the Huffington Post, Buzzfeed and Gawker.
In September 2015, a new feature of Amazon Web Services called DynamoDB overloaded servers with metadata requests knocking Reddit, Tinder, Netflix, IMDB and many other websites and apps offline for seven hours.
Chancellor’s Memorandum #42 (CM – 42) Information Technology (IT) Infrastructure states:
“All users of the SYSTEM IT infrastructure shall NOT use non-LSUHSC E-mail to conduct official LSUHSC business unless authorized by the Chancellor.”
All faculty, staff and students are responsible for information sent to and from their lsuhsc.edu email addresses. Do not use any email system other than “@lsuhsc.edu” to send or receive LSUHSC-NO related information including protected or restricted information. Emails from one “@lsuhsc.edu” email address to another are protected by a variety of security measures and are considered safe for protected and restricted information. Emails can be sent securely from the lsuhsc.edu to other domains using a form of encryption called Transport Layer Security (TLS). To find out if the intended destination of your email supports this encryption refer to the Encrypted Email - Site to Site List.
Outgoing encrypted email connections rated at 100% are secure.
If the domain is not secure, the information can be transferred using LSU Health FileS. (Add this link to your browser favorites! )
Do not automatically forward email from your lsuhsc.edu account to a non-LSU email system. Email in your LSUHSC inbox may contain sensitive information. If it is sent to a non-LSU email system that does not have the appropriate security precautions in place, a data breach may result.
LSUHSC-NO Servers are:
- Located in Louisiana
- Protected by a comprehensive set of technical, physical and administrative safeguards
- Regularly backed up to tape
- Protected by a tested disaster recovery plan
Requirements for Using Cloud Services for LSUHSC-NO Data
A written contract must be executed with the cloud service provider to ensure that:
- Any data stored with the cloud service provider (whether in files or emails) remains under the jurisdiction of U.S. laws.
- The cloud service provider agrees to the confidentiality and security requirements that apply to LSUHSC-NO data under federal and state laws and regulations.
- The cloud service provider guarantees that the data will be readily available.
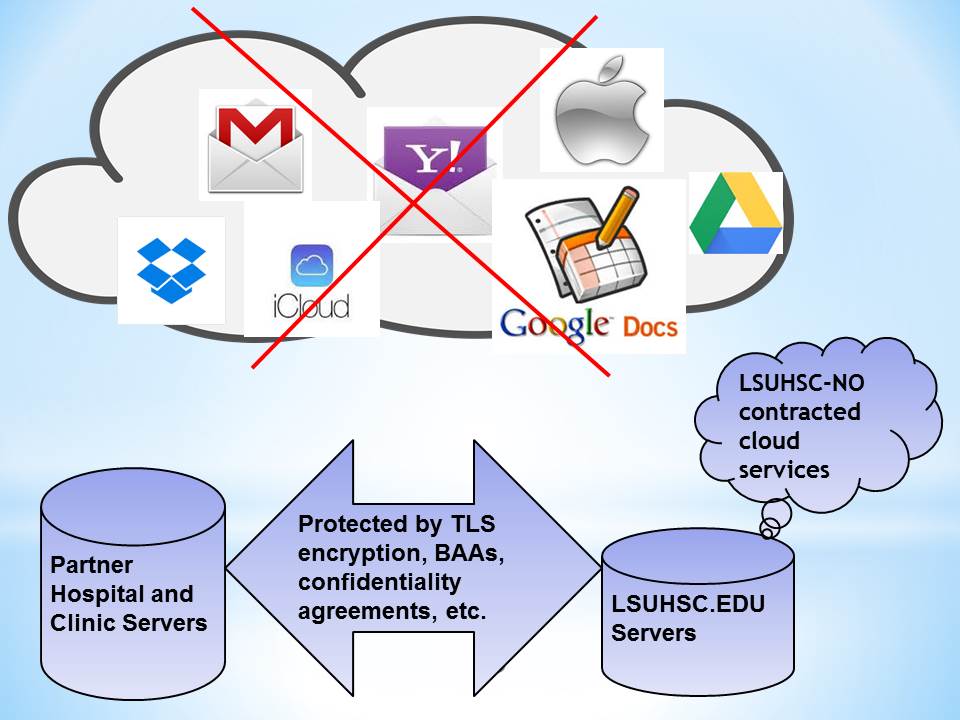
(Click or tap image for expanded view.)
Use LSUHSC-NO I.T. Services
The safest thing to do is use LSUHSC-NO IT services for your data needs.
- If you need to share files, use LSU Health FileS instead of Box or DropBox.
- If you need a resource emailbox (e.g. “ChiefResidents” contact LSUHSC Information Security and get "ChiefResidents@lsuhsc.edu" instead of "ChiefResidents@GoDaddy.com."
- If you need to exchange files with someone outside the LSUHSC network use LSU Health FileS instead of Dropbox to transfer protected or restricted information.
Keep Personal and Work Activities Separate
- Use personal email addresses for personal communications.
- Always send work or school related emails via your lsuhsc.edu address.
- NEVER send patient information to your personal email address.
If you access your email accounts on your phone:
- Never “combine” your inboxes. You run the risk of sending emails meant for your “@lsuhsc.edu” account on your personal account.
- Use separate inboxes, one for your “@lsuhsc.edu” email and one for your personal email.
- As an alternative, download a separate email app to use for your “@lsuhsc.edu” email account.
Meet Sara

Sara has started a student group to help individuals with transportation to their healthcare appointments. Her volunteers need to access a schedule showing the patient’s name, address, clinic address, and reason for the visit so they can get the patients to their appointments on time.
Should Sara?
- Set up a calendar in Doodle because its free, it’s easy and everyone can access it?
- Contact her IT supporter for help in setting up an on-line calendar on the LSUHSC network?
The answer is . . .
Contact her IT supporter for help in setting up an on-line calendar on the LSUHSC network.Because the information includes the reason for the visit, the information could be PHI and therefore it is Protected Information under PM-36. Sara needs to ensure that appropriate protections are in place for that information. The easiest way to do that is to keep the information on the LSUHSC network.
Meet Dr. Jadarius

Dr.Jadarius is chief resident this year. To help with the communications with all the residents in the program he’d like to set up an email address called Chief Resident that can be used to send out announcements and to serve as a central point for scheduling requests, etc.
Should Dr. Jadarius?
- Set up an email account on one of the free cloud email services? It’s quick. It’s easy. And ChiefResident@Rocketmail.com sounds pretty cool.
- Contact LSUHSC Information Security to set up the email address, ChiefResident@lsuhsc.edu?
The answer is . . .
Contact LSUHSC Information Security to set up the email account, ChiefResident@lsuhsc.edu.
Even though the email account will only be used for administrative purposes, those purposes are related to Jadarius’ duties as an LSUHSC chief resident and as such are official business of the university. In accordance with CM-42, that must be done using an lsuhsc.edu account.
Meet Dr. Lapayerre

Dr. Lapayerre is a member of the LSUHSC-NO faculty. To help him with his busy schedule, he relies heavily on his state-of-the-art smartphone.
One day a colleague, Dr. Smith, to whom he had referred a patient, asked for some additional information. Dr. Lapayerre sent a detailed reply including the H&P, test results, and current medications from his smartphone. Dr. Smith replied by saying, “Who is lapdog1975@prodigy.com and why does he know so much about your patient?”
Dr. Lapayerre is aghast! lapdog1975@prodigy.com is his personal account. He could have sworn he sent the email from his lsuhsc.edu account. What went wrong?
What Went Wrong?
To ensure he did not miss anything, Dr. Lapayerre combined the inboxes of both his personal email account and his lsuhsc.edu account.
When Dr. Smith’s inquiry arrived, Dr. Lapayerre had been in the middle of responding to an email from his wife. When he switched to respond to Dr. Smith, he forgot to check the “From:” address to ensure it said “@lsuhsc.edu.”
As a result, the information on his patient has been stored on the prodigy.com servers.
What does he do now?
Immediately:
- Make a note of the patient identifying information and health information that was inadvertently stored on prodigy.com
- Delete all occurrences of the information from prodigy.com.
- Using his lsuhsc.edu email account, notify the LSUHSC-NO Privacy Officer with a summary of what happened.
The privacy officer will conduct a risk assessment to determine if the patient will need to be notified of the disclosure in accordance with the HIPAA Breach Notification Rule.
To prevent a recurrence, Dr. Lapayerre should install separate mail apps on his phone, one set up to access only his personal email account and one set up to access only his LSUHSC email account.
Data Breaches
A data breach occurs when sensitive information is accessed by unauthorized persons.Federal and State laws require that persons whose personal, financial, or health information is compromised by a data breach must be notified that their information has been disclosed.
Information that is encrypted is exempt from these notification requirements.
Data breaches can expose LSUHSC and its employees to civil and criminal penalties.
Civil monetary penalties for data breaches range from $100 to $50,000 per record.
Criminal penalties include imprisonment for up to ten years.
The employee’s or student’s department will be held responsible for any data breaches that occur and will bear the expenses incurred in mitigating a breach.
Getting Help
If you have any questions, please contact the Office of Compliance Programs by:
- Email: nocompliance@lsuhsc.edu
- Phone: 504-568-5135
- In Person: RCB, suite 807
- Website