SSL Intermediate Certificates
At LSU Health New Orleans, we receive SSL Certificates issued through InCommon. In order for these certificates to be trusted by the client, intermediate certificates must be installed which chain to a root certificate that is trusted by the client. A certificate chain allows for a level of trust from the certificate, through one or more intermediates, to the root level which is contained on the client side. This process increases the security of certificates issued through the root level certificate.
Where Are Intermediate Certificates Installed?
Intermediate Certificates must be installed on web servers or SSL accelerators in front of the web servers. This is necessary for clients to be able to trust the certificates.
Where Do I Get the Intermediate Certificate?
Intermediate Certificates can be found when downloading InCommon SSL certificates. Choose the x.509 Intermediate(s)/Root(s) option. One certificate will download containing three certificates.
The certificate can also be downloaded from https://www.incommon.org/certificates/repository/sha384%20Intermediate%20cert.txt. When the file is downloaded, rename the extension to .cer. If the file loads in the browser, copy the contents to a new file with a .cer extension. This certificate contains both an intermediate certificate for InCommon and an Intermediate for UserTrust.
How Do I Install the Intermediate Certificate?
If using the intermediate from the x.509 certificate, copy the third certificate from the file into a new file with a .cer extension. Otherwise, use one of the other options.
Windows
Open mmc, add the Certificates snap-in, choose Computer->Local Computer. Then, install this certificate into the Intermediate Certificates section.
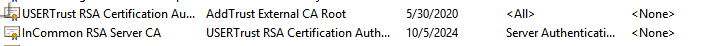
The following intermediate certificates will be added:
Other Systems
On some systems, the certificate will need to be manually chained (all certificate strings in one file) to the Intermediates before it is installed. The ordering required is dependent upon the system it is being installed on. On other systems, the Intermediate certificate is installed in a separate location from the certificate.
Testing
Test through ssllabs.com
-
Submit the URL
-
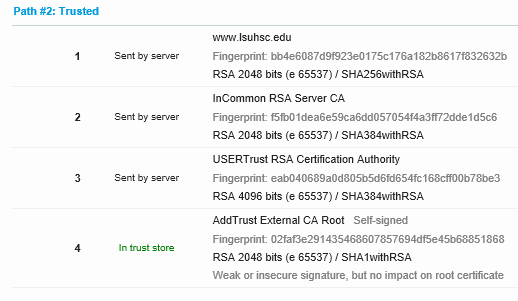
Success appears like this under certification paths:
-
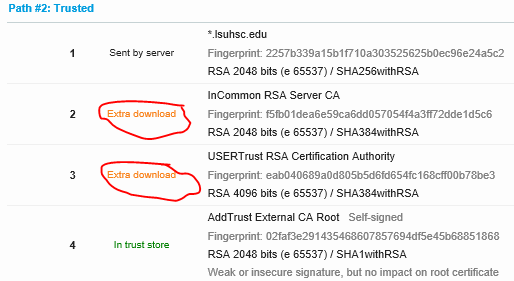
Chaining errors appear like this (with one or more “Extra download” descriptions):
Testing Through Linux Command
-
Execute:openssl s_client -connect domainname:443 -CApath /etc/ssl/certs/
-
A successful certificate chain can be seen below (unsuccessful chain would be missing part of the chain):
Certificate chain (Trusted)
- 0 s:/C=US/postalCode=70112/ST=Louisiana/L=New Orleans/street=433 Bolivar Street/O=Louisiana State University/OU=LSU Health Sciences Center New Orleans/CN=intranet.lsuhsc.edu
- i:/C=US/ST=MI/L=Ann Arbor/O=Internet2/OU=InCommon/CN=InCommon RSA Server CA
- 1 s:/C=US/ST=MI/L=Ann Arbor/O=Internet2/OU=InCommon/CN=InCommon RSA Server CA
- i:/C=US/ST=New Jersey/L=Jersey City/O=The USERTRUST Network/CN=USERTrust RSA Certification Authority
- 2 s:/C=US/ST=New Jersey/L=Jersey City/O=The USERTRUST Network/CN=USERTrust RSA Certification Authority
- i:/C=SE/O=AddTrust AB/OU=AddTrust External TTP Network/CN=AddTrust External CA Root
Note: There is no need for a third with AddTrust because clients have AddTrust in Trusted Root by default and therefore AddTrust trusts USERTrust trusts InCommon trusts certificate.
Certificate chain (Untrusted)
- 0 s:/C=US/postalCode=70112/ST=Louisiana/L=New Orleans/street=433 Bolivar Street/O=Louisiana State University/OU=LSU Health Sciences Center New Orleans/CN=*.lsuhsc.edu
- i:/C=US/ST=MI/L=Ann Arbor/O=Internet2/OU=InCommon/CN=InCommon RSA Server CA
Testing Through BlackBerry
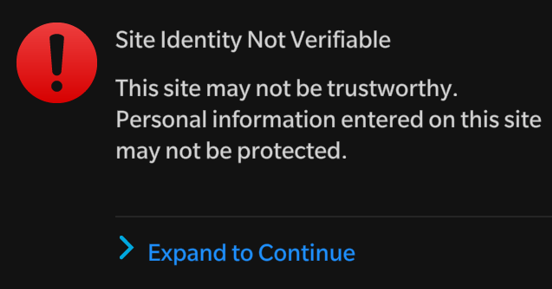
Load the site through the BlackBerry. If there is a problem, click on the exclamation mark in the address bar to see the following error messages:
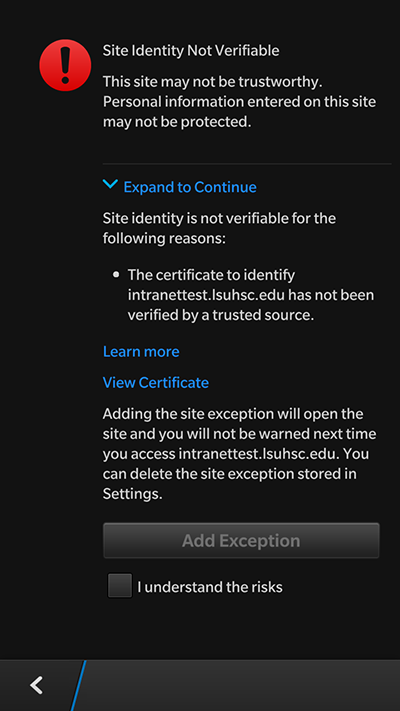
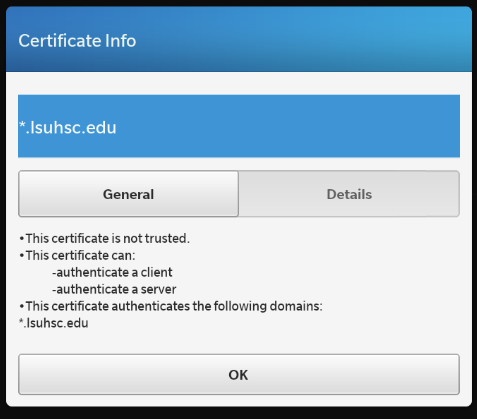
Correcting Chaining Errors
Windows 2008 R2
References
-
InCommon Ticket:#UKX-378-67050
- < >
Click Start, and then click Run.
-
Type gpedit.msc, and then click OK.
-
If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Continue.
-
Double-click Administrative Templates, double-click System, double-click Internet Communication Management, and then click Internet Communication settings.
-
Double-click Turn off Automatic Root Certificates Update, click Enabled, and then click OK.
-
Close the Local Group Policy Editor.
Delete UserTrust Root Certificate
-
Open mmc
-
Add Certificates
-
Local Computer
-
Navigate to Certificates->Trusted Root Certification Authorities->Certificates
-
Delete USERTrust RSA Certification Authority
Reboot
- After setting group policy and deleting any USERTrust Root Certificates, reboot the system. After the reboot, retest the certificates again.
Devices
-
For other devices like Linux systems or VPN, etc., be sure to include the entire chain as part of the certificate that is added to the system.Different devices require a different order of the certificates in the chain.
